Why would you want to install a private VPN Server?
The major purpose of having a vpn server is being able to access your local network from any place in the world in a secure manner. Looking at the nature of a VPN connection, which can forward all the traffic from the remote device to a VPN Server, there might also be other reasons why someone would want to use a VPN connection. For the purpose of this article, I am going to concentrate on solely accessing our home or business local network from anywhere in the world.
The process of setting up a VPN server can be somewhat difficult for a beginner. When I had done it for the first time it took me hours to have the task completed. No fear though, in this guide I will go through all the necessary steps and I will try to be as prompt and concentrated as possible.
Firstly let’s see what we need in order to accomplish this task.
Requirements
- Two separate Linux Ubuntu 20.04 installations
- Windows with PSCP command installed
We will be using two linux installation due to security reasons. On one server we will will run VPN server the other one will be used as a key and certificate signing authority. Having the two separated increased the overall security.
For the purpose of this guide, I will be using following names for the server:
CAServer: for certificate authority
VPNServer: for open-vpn server
Since we are going to be operating on two server installations I find it much easier to manage those from my Windows 10 installation via CMD using ssh protocol. We are also going to transfer files between Linux and Windows. In this case we are going to need PSCP on Windows.
Click this link for SSH installation on Linux
Click this link for PSCP on Windows
Steps
- Creation of Certificate Authority (CA), Server key and Certificate
- Server Certificate Signature
- Creation of client key & certificate and signing of the client certificate
- Creation of TLS authentication key and DH Parameters
- Open VPN firewall rules
- Open VPN Server configuration
- Creation of client OVPN file
- User authorisation against Windows Active Directory (optional)
1. Creation of CA, Server key and certificate
Assuming that you have already created two independent servers we are going to perform operations on the CAServer first. We will need to install the easy-rsa package, which will serve as out certificate authority. We are also going to update our package repository before hand.
$ sudo apt-get update && sudo apt-get -y install easy-rsa
Placing ‘-y’ in the command line simply saves us time by accepting any options before hand.
As a next step we will use the in-built command of rsa to create a folder which contains all configuration files and any tools that come with it. In our case lets create a folder called rsa_certificate
$ make-cadir rsa_certificate
Let’s change directory to the newly created folder
$ cd rsa_certificate
Let’s list the content of the new folder
$ ls
you should be able to see a file named vars. We will open this file using nano command
$ sudo nano vars
edit the content of the file with your appropriate details e.g:
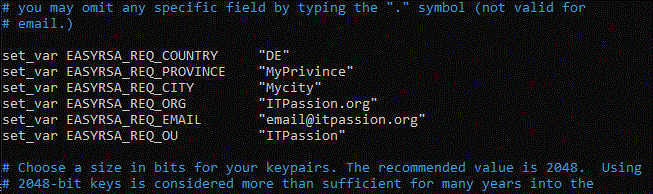
save the changes using Ctrl+x and then confirm by pressing enter.
Our next step ist to create a public key infrastructure. For this we are going to initiate a built-in command of easyrsa which will create a new folder called PKI with all the necessary tools.
$ ./easyrsa init-pki
Let us now create/generate our server certificate (CA) and server key. Execute the command below. You will be asked to enter a password for the ca key as well as a common name. If you leave the common name blank and press enter an automatic name will be assigned such as Easy-RSA CA.
$ ./easyrsa build-ca
The command generates two files inside the /pki folder.
ca.crt
ca.key (/pki/private/)
These files are: a public certificate and key used to sign the open-vpn server and clients certificates. In other words, each certificate, the server and client, need to receive a signature so that later a connection can take established between the vpn client and the vpn server. The ca.key is very important, therefore make sure you keep it safe. Also never forget the password you made before.
Now, that we have both the certificate and its key let us do the same for our Open-VPN server.
Let’s generate both and get a signature for them from our certificate authority (easy-rsa).
Switch over to the VPNServer. Install openvpn and easy-rsa
$ sudo apt-get update && sudo apt-get -y install openvpn easy-rsa
As before:
$ cd
$ make-cadir rsa_certificate
$ cd rsa_certificate
$ sudo nano vars
$ ./easyrsa init-pki
After going through these steps we will want to create a certificate and a key. These certificates are somewhat different because these are requests for a signature and the signature will be provided by the authentication server. Therefore also a slightly different command.
$ ./easyrsa gen-req server nopass
The above command will generate a request certificate with no password and with the above name ‘server’. You can call it whatever u want, but I will stick to the simplicity of calling these as server and client for ease of recognition.
The generated key and certificate will be placed in:
req: /home/’yourusername’/rsa_certificate/pki/reqs/server.req
key: /home/’yourusername’/rsa_certificate/pki/private/server.key
We will have to move the key file into /etc/openvpn/
$ sudo mv pki/private/server.key /etc/openvpn
The request must be sent to the certificate authority (in this case CAServer) so that it can be signed. Use following command:
$ scp pki/reqs/server.req 'yourusername'@'IPaddress_of_your_CAServer':/home/'yourusername'/
Note: without the apostrophe signs
Now, we move back to CAServer in order to sign the request
2. Server Certificate Signature
Being on your CAServer change folder to your home directory if you haven’t done it yet. Inside you should find the transferred file from the previous step.
$ cd $ ls
rsa_certificate server.req
Let us navigate to rsa_certificate folder
cd rsa_certificate
Now let’s import the certificate request. We are going to use a function of the easyrsa import-req
we use following syntax:
import-req <request_file_path> <short_basename>
$ ./easyrsa import-req /home/'your_user_name'/server.req server
It should return following output:
Note: using Easy-RSA configuration from: ./vars Using SSL: openssl OpenSSL 1.1.1d 10 Sep 2019 The request has been successfully imported with a short name of: server You may now use this name to perform signing operations on this request.
Now, since we have imported the request, it needs to be signed. To do so we will use sign-req with short_basename syntax.
$ ./easyrsa sign-req server server
Upon execution we are going to be asked to provide the CA key password that we had previously set up.
Let us delete the server.req
$ cd
$ ls
rsa_certificate server.req
$ rm server.req
$ ls
… and copy the server.ctr & ca.crt (public certificate) back to the vpnserver
$ cd rsa_certifcate/pki/issued/ $ scp server.crt yourusername@your_vpnserver_ip:/home/yourusername $ cd rsa_certificate/pki/ca.crt $ scp ca.crt yourusername@your_vpnserver_ip:/home/yourusername
On the VPNServer lets move/copy the files into /etc/openvpn/
$ sudo cp server.crt /etc/openvpn $ sudo cp ca.crt /etc/openvpn
3. Client Certificate key and certificate request
We are going to repeat the above steps in order to generate a key for the client and a client certificate.
$ cd rsa_certificate $ ./easyrsa gen-req client nopass
Once asked to enter a base name type client. The two files will be created in the following location:
req: /home/’yourusername’/rsa_certificate/pki/reqs/client.req
key: /home/’yourusername’/rsa_certificate/pki/private/client.key
Now copy the request to the CAServer.
$ scp pki/reqs/client.req yourusername'@'IPaddress_of_your_CAServer':/home/'yourusername'/
Switch over to the CAServer now and import the request
$ cd /rsa_certificate $ ./easyrsa import-req /home/'yourusername'/client.req client
Now as it is time to sign the imported certificate request. You will be prompted to enter the CA Certificate key password which you have created at the beginning
$ cd $ cd rsa_certificate $ ./easyrsa sign-req client client
The client signed certificated will be created in
Certificate created at: /home/’yourusername’/rsa_certificate/pki/issued/client.crt
Let us copy it back to the openvpn server:
$ scp pki/issued/client.crt yourusername'@'IPaddress_of_your_OpenVPNServer':/home/'yourusername'/
Delete the request file
$ cd $ rm client.req
Now let us move all client related files into a folder called client. For this purpose we are going to create a new folder.
This is being done on the VPNServer now!
$ cd $ mkdir client $ cd rsa_certificate $ mv pki/private/client.key /home/'yourusername'/client/client.key $ cd $ mv client.crt /home/'yourusername'/client/client.crt
Now our new client certificate and client key are in one folder for the ease of access.
4. Creation of the tls key (ta.key) and Diffie-Hellmann parameters (dh2048)
Open Vpn integrates tls-auth in order to further improve security. With the following steps we are going to generate a ta.key. Make sure to switch back to your VPNServer.
$ cd /rsa_certificate $ openvpn --genkey --secret ta.key
Having done so let’s now generate a Diffie-Hellmann key used in the transfer of crypto key over insecure and public channels. We will create the key and move it form its default location the openvpn folder while changing its name to dh2048.pem
$ cd /rsa_certificate $ ./easyrsa gen-dh
Let’s move both files to Openvpn folder
$ cd rsa_certificate $ sudo cp ta.key /etc/openvpn $ cd $ cd rsa_certificate/pki/ $ sudo cp dh.pem /etc/openvpn/dh2048.pem
5. VPN Firewall rules
We are going to set up some firewall rules of the Open Vpn server now. This is important to further increase the security of the server. Before we proceed to ufw rules lets first activate IP forwarding on our VPNserver.
$ cd /etc/ $ sudo nano sysctl.conf
after opening the file find and uncomment the line
net.ipv4.ip_forward=1now let’s reload the setting
$ sudo sysctl -pNow we are going to modify the ufw by allowing the forwarding. We navigate to /etc/default/ufw file and change Default_Forward_Policy to accept.
$ sudo nano /etc/default/ufw
# Set the default forward policy to ACCEPT, DROP or REJECT. Please note that
# if you change this you will most likely want to adjust your rules
DEFAULT_FORWARD_POLICY="ACCEPT"As the next step we are going to add a routing rule, which will be added prior to any existing firewall rule. To do so you will need first to check the exact name of the interface used for the connection and secondly to add the rule to a file called before.rules
… so let’s check the Interface name first
$ ifconfig

in my case the interface is called enp03. In many cases it might be called eth0.. Make sure to check this out.
Now let’s edit before.rules
$ sudo nano /etc/ufw/before.rules
add the line at the beginning of the file
*nat:POSTROUTING ACCEPT [0:0]-A POSTROUTING -s 10.8.0.0/8 -o enp0s3 -j MASQUERADECOMMIT
After having done so we are going to allow openvpn through the firewall, restart the firewall and finally restart openvpn server
$ sudo ufw allow openvpn$ sudo ufw disable$sudo ufw enable$ sudo systemctl restart openvpn $ sudo systemctl enable openvpn
6. Open VPN Configuration
We have conducted many steps by now. Now is the time to configure the vpn server so that it actually accepts incoming connections. For this we will use a sample configuration file delivered with the server installation. File should be found in: /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz
Let’s use the zcat command for compressed files and resave it as a new file
$ cd /usr/share/doc/openvpn/examples/sample-config-files/
§ zcat server.conf.gz | sudo tee /etc/openvpn/server.conf > /dev/nullWe can now work on the newly generated file inside the /etc/openvpn/server.conf file.
So let us ‘nano’ the file.
$ sudo nano /etc/openvpn/server.conf
Now we have to make sure that the file contains the right names for our ca, cert, key and dh. We have created them before and placed inside the /etc/openvpn/ folder. Check it
ca ca.crtcert server.crtkey server.keydh dh2048.pem
Now find lines user nobody and group nobody. Unhash these. This will allow anyone with the client configuration file to connect to the vpn server. If you are willing to have user authentication against an Active Directory server you can find the steps in chapter 8.
Another parameter worth changing is on line 192.
push "redirect-gateway def1 bypass-dhcp"
This will tell the server to forward your default gateway through the vpn server. This option is great for geo-locked content. For example while visiting a foreign country for holidays it will in virtually place your laptop at home location :-). Isn’t that cool? Think of some other benefits such as your favorite movies that are geo-locked!!
Worth considering is line 200 and 201
push "dhcp-option DNS 208.67.222.222"
push "dhcp-option DNS 208.67.220.220"
I use this myself.. If you have local network with server and devices, this option will save you typing in all the individual IP addresses as now you can us DNS Names.
So as a next step we must verify that we have all the necesary files inside /etc/openvpn folder. We have been moving them into that folder along the way. So lets check:
$ ls /etc/openvpn ca.crt dh2048.pem server.conf server.crt server.key ta.key
These files should be found there. If you are missing any, go back and verify the steps.
There is one more step to go in this chapter but before we proceed lets copy the ta.key file into our /client folder. We normaly would not need to do this, but if you intend to use OpenVPNconnect App on your smart phone, this file might be needed. Well it was in my case at least.
$ cp /etc/openvpn/ta.key /client
Now as a final step let us change permissions on the etc/openvpn to root user. We do it to seal this folder from unauthorized access. Remember that if u decide later on to move this folder or the files inside of it to a different location you will have to reapply new permission or to elevate your user to root.
$ sudo chown -R root:root /etc/openvpn
7. Client configuration file
In chapter 3 we have created a folder called /client. We will use this folder to store all client files. Until now we have placed the client.key, client.crt, ta.key
Now we need to place inside the folder the client.conf file. We will use a template from /usr/share/doc/openvpn/examples/sample-config-files/client.conf
$ cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf ~/client
Let us edit the copied file
$ cd /client $ sudo nano client.conf
The first entry to be edited is on line 42.
remote my-server-1 1194
please replace ‘my-server-1’ with the actual external IP of your server or a host name e.g. itpassion.org. you can also replace the default port number. makes sure to forward this port on your router/firewall/gateway.
The next two entries that need uncommenting are:
;user nobody ;group nogroup
Just remove the semicolon ; Please note that if u decide to use user authentication we are going to set this up via the openvpn server. This will be explained in the next chapter though.
As the last step we will be adding some lines to the bottom of the file
<ca>
# Copy and paste the content of the ca.crt file
</ca>
<cert>
# Copy and paste the content of the client.crt file
</cert>
<key>
# Copy and paste the content of the client.key file
</key>
key-direction 1
<tls-auth>
# Copy and paste the content of the ta.key file
</tls-auth>
You will be placing the long chain of random signs from ca.crt, client.crt, client.key, ta.key. As you might remember these are stored on the VPNServer in the /home/client folder.
Once this has been completed you simply secure copy the client.config to your windows installation. Check this post to find out how to transfer files between linux und windows.
Once this has been done please rename the client.config to any desired name with *.ovpn extension. This file needs to be placed inside the OpenVPN installation folder. In my case this was “C:\Program Files\OpenVPN\config”. This would actually be all to establish a secure connection to your network. The negative point is that if any one got in position of this configuration file, he would be able to connect without user prompt. Since you already have setup a VPN server I strongly recommend to also run an Active Directory for your local network which manages all your local network user permissions. Therefore in the next chapter I will concentrate on explaining how to set up VPN User Authentication.
8. OpenVPN user authentication against Active Directory
Due to the length this chapter has been moved to a separate Post. Please follow this post to read more.

Leave a Reply