The Purpose of this article is to go thought the setup process of UFW Firewall as well as to learn some essential commands for managing your firewall rules
Requirements
- Ubuntu 20.04
- Sudo non-root user
Please note that most of the commands apply also to previous versions of ubuntu. In this tutorial we are concentrating on IPv4 rules. Should you be using IPv6 on your server make sure to also enable IPv6 in UFW
UFW installation
In order to install the fire wall run this command
$ sudo apt update $ sudo apt install ufw
Now let us enable IPv6 (if needed) by editing the default configuration file
$ sudo nano /etc/default/ufw
please make sure that the value of IPv6 is set to yes
IPV6=yes
Setting up default UFW policies
When freshly installing an UFW firewall all of the policies are default and set to allow outgoing traffic but block incoming traffic. If you have had already an UFW running and wish to set all the default rules to default settings you can execute this command.
$ sudo ufw default deny incoming $ sudo ufw default allow outgoing
we can prove the current state of the firewall with the next command
$ sudo ufw status verbose
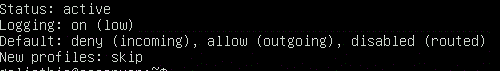
we receive a return showing us that the ufw is active allowing outgoing connections and denying incoming. Should you receive a status message as inactive you can enable the firewall with the following command.
$ sudo ufw enable
analogically should you wish to disable the firewall just type
$ sudo ufw disable
and further more a restart can be done by combining the two
sudo ufw disable && ufw enable
or
sudo systemctl restart ufw
Since by default there are no individual rules set let us add a rule for SSH so that we could manage our server form another Client via the ssh protocol which uses port 22 as default. The command “enable” switches the firewall permanently on, also after a system reboot.
Allowing SSH connection through UFW
As mentioned before we can allow the application directly or allow the specific port. First option will automatically open the necessary port therefore:
sudo ufw allow ssh sudo ufw allow 22
both will allow communication on port 22 for us.
Please note that if you have specified a different port for ssh to listen on make sure to manually allow that port on ufw. For example if you set ssh on port 6666, analogically the command would be like this:
$ sudo ufw allow 6666
Allowing Specific Connections
You have seen by now how to allow a specific port. We can additionally configure our UFW to allow or block specific:
- ip addresses
- range of ports
- subnets
- network interfaces
Let us have a look at the first one. Imagine we would like to join our home server from work so that you could manage it any time you desire. Presuming you know what the external IP of your work is , which in our example would be 185.234.123.45 then we could add a rule allowing connection to our server for this IP only over the SSH port. Our command in this case looks like this.
$ sudo ufw allow from 185.234.123.45 to any port 22
should you wish to allow the specific IP to enter the whole network just leave the port out.
$ sudo ufw allow from 185.234.123.45
A word of advice:
It is always best to have as few ports open as possible. Lowering the number of open ports lowers the risk of security breach. Try accessing your local network through a secure connection such as VPN. The process of setting up such a connection is quite straight forward. If interested follow this link.
Subnet
Should you want to allow or deny a whole range of IP addresses, we could do it by specifying a netmask. For example we wish to block a whole IP range from 192.168.1.1 to 192.168.1.254. In order to do so we would write:
$ sudo ufw deny from 192.168.1.0/24
analogically we can also allow this subnet to connect to specific port.
$ sudo ufw allow from 192.168.1.0/24 to any port 6666
We also have the possibility to narrow the allow/deny rule to a specific protocol. For example we would like to only allow UDP traffic on port 6666. We just replace have to replace “any” with “allow”
$ sudo ufw allow from 192.168.1.0/24 to UDP port 6666
Range of Ports
What if instead of a IP range we would like to add a rule for a port range. Let’s presume an app requires ports 5000 to 5005 over UDP. The syntax looks as follows:
$ sudo ufw allow 5000:5005 /udp
analogically you can allow or deny any range of ports as desired.
Network Interface
But what if we would like to add rules for specific netwrok interfece. Let’s presume we have multiple NICs on our server. We would like to allow external traffic to our server only via NIC 1. First we need to find out the interface name on ubuntu. We do it by running ‘ifconfig’ command.
$ sudo ifconfig

in my case the desired interface has a name of enp0s3. We are going to use this interface to allow external http traffic to our server.
$ sudo ufw allow in on enp0s3 to any port 80
Deleting Rules
Having added rules we might want to also delete them too. The best way to do it, is to first get a listing of all the applied rules in a numbered way. We achieve this by typing:
$ sudo ufw status numbered
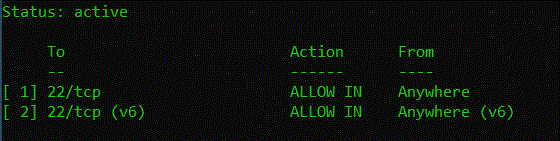
In my case there are two available rules numbered as 1 and 2. I would like to get rid of the rule for IPv6 connections. To do so we just type:
$ sudo ufw delete 2
Resetting or Disabling UFW
Let’s summaries the few commands that we had previously used for disabling/restarting or resetting of the ufw process.
In order to disable UFW use:
$ sudo ufw disable
In order to enable UFW use:
$ sudo ufw enable
In order to reset UFW use:
$ sudo ufw reset
In order to restart USW use:
$ sudo systemctl restart ufw